In a WebShell attack, cybercriminals inject a malicious file into the target web server’s directory and then execute that file from their web browser.
After performing a successful Web Shell attack, a cybercriminal can gain access to sensitive resources, recruit the target system to a botnet, or create a path for malware or ransomware.
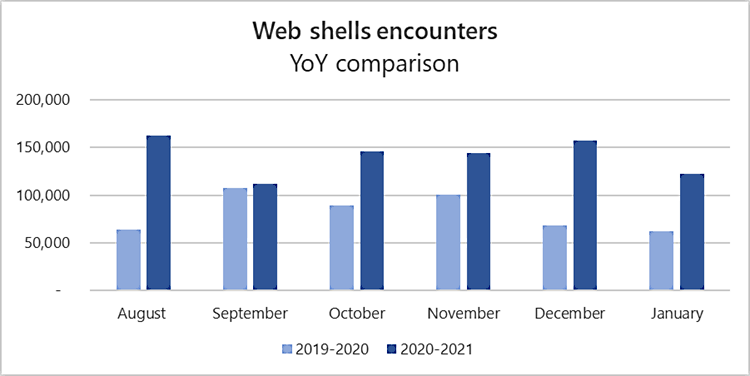
If you do not have defense strategies against this cyber threat, your system is at high risk of being exploited. According to Microsoft, monthly shell-based web attacks have doubled in the past year alone.
What is WebShell Attacks?
A webshell is a malicious script written in one of the popular web application languages - PHP, JSP, or ASP. They are installed on the web server operating system to facilitate remote administration.
When armed, the web shell can allow an attacker to modify files and even gain access to the root directory of the targeted web server.
Servers that are connected or not connected to the Internet (such as a resource host) can be victims of Web Shell attacks.
Web Shell attacks are a convenient cyber attack tactic because their implementation requires no additional programs. A communication channel can simply be done via the HTTP protocol in a web browser – that’s why prioritizing the HTTPS protocols is so important.
Here is a brief introduction to the inspectors:
Webshell obtains certain permissions of the server through the open port of the server.
How Do WebShell Attacks Work?
WebShell is a malicious script often used by hackers. The principle is to use malicious code running in the environment of the Web server itself. It is a way to use the web service program to control the server through the upload of the WebShell script.
Taking the PHP language as an example, you only need to write a simple PHP code file and upload it to the website directory to control the website server, including reading the database, deleting files, and modifying the homepage. Such a simple statement can open the door for hackers to execute arbitrary code at will.
How to defend against WebShell attacks?
It’s much easier to address the vulnerabilities that facilitate web shell injection than it is to intercept web shell attacks.
The following suggested controls and security tools should be used to locate and remediate all possible web shell injection points in your IT ecosystem.
- Configure necessary firewalls and enable firewall policies to prevent exposure of unnecessary services and provide conditions for attackers to exploit.
- Strengthen the security of the server, for example, disable the remote desktop function, change the password regularly, prohibit the use of the highest privileged user to run programs, and use the HTTPS encryption protocol.
- Strengthen permissions management, set permissions for sensitive directories, limit script execution permissions in uploaded directories, and do not allow configuration execution permissions.
- Install the Webshell detection tool, immediately isolate and kill the suspicious Webshell traces found according to the detection results, and check for vulnerabilities.
- Check for loopholes in the program and fix the loopholes in a timely manner. You can troubleshoot vulnerabilities and intrusion causes with the assistance of professionals.
- Always back up important files such as databases.
- It is necessary to maintain routine maintenance and pay attention to whether there are executable script files of unknown origin in the server.
- Use the whitelist mechanism to upload files. Those not in the whitelist are prohibited from uploading. The upload directory permissions follow the principle of least permission.



























