There is an 11-fold increase in phishing attacks exploiting SaaS Platforms. Attackers are abusing legitimate SaaS platforms in order to create phishing sites. Attackers are abusing legitimate software-as-a-service (SaaS) platforms to create phishing sites, researchers have found, according to a report from Palo Alto Networks Unit 42, which shows that from June 2021 to June 2022, There has been a massive 1,100% increase in such abuses.
SaaS offers several advantages for phishing, including evading detection by email security systems, enjoying high availability, and not having to learn to code to create legitimate-looking websites. Furthermore, since the SaaS platform simplifies the process of creating new sites, attackers can easily switch to different themes, and expand or diversify their operations.
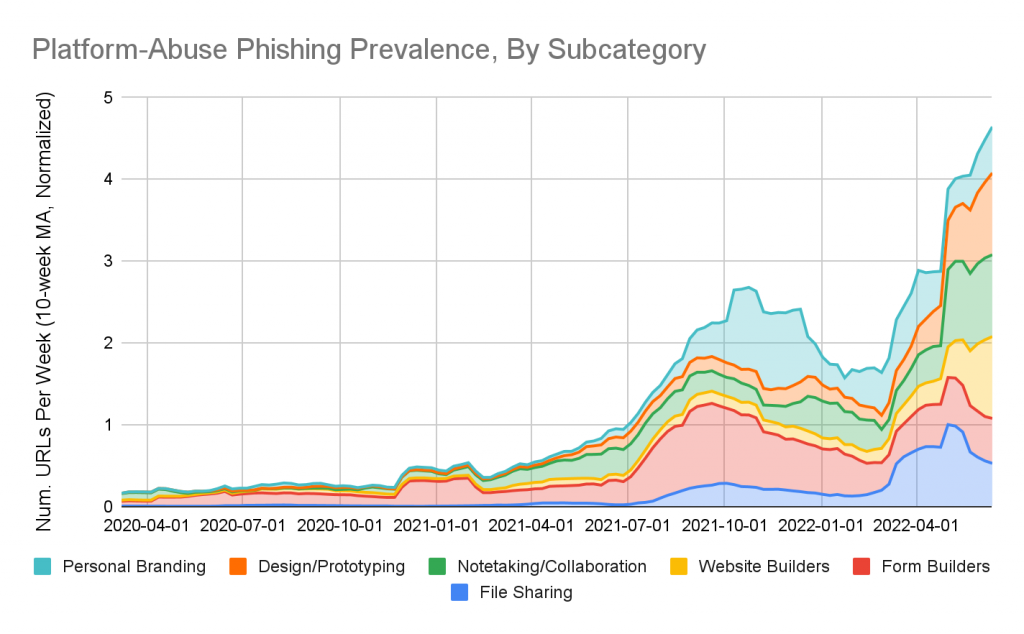
Unit 42 divided the abused platforms into six categories: file sharing, survey formulators, website generators, note-taking, and document-writing platforms, and personal profiles. Palo Alto Networks recorded abuse growth across all categories.
The Unit 42 report explains that in most cases, attackers host their credential-stealing pages directly on the abused service, and in some specific cases, the login page hosted on the abused service does not contain the credential-stealing form itself, Instead, the attacker takes the victim to another site through a redirection step.
Phishing sites can be hosted on a bulletproof hosting provider (BPH) that does not respond to takedown requests, so phishing actors follow this practice to increase campaign uptime while sacrificing conversion rates. If the final credential-stealing page is removed, the attacker can simply change the link and point to the new credential-stealing page, keeping the phishing behavior going.
Research suggests that preventing abuse of legitimate SaaS platforms is very difficult, which is why SaaS is so suitable for phishing campaigns. For users, it’s also important to keep in mind that the website URL is legitimate when asked to enter account credentials.



























