Internet connectivity has enabled everyone to create an online identity. Companies and businesses are taking advantage of this opportunity to expand worldwide. If you don’t want your or your company’s data to be accessible to malicious actors or be available on the dark web, the most effective practice is to proactively find and secure your entry points in your IT infrastructure before hackers don’t. Here we will discuss vulnerability scanners that are easy to use and will save you a lot of time and effort.
In the field of network security and cybersecurity, vulnerability scanning provides a very critical service, and in cooperation with others, it can increase the security of a network. When it comes to vulnerability scanning, easy-to-use tools are essential, so what are web vulnerability scanning tools? This article recommends the most popular web vulnerability scanning tools. Come and take a look, but first, let’s see what’s the Importance of Vulnerability Scanning
The Importance of Vulnerability Scanning
Vulnerability scanning is the process of identifying, evaluating, mitigating, and reporting security flaws in an organization’s infrastructure and software. Finding and fixing vulnerabilities manually can be a tedious, time-consuming, and labor-intensive task. Thus, vulnerability scanners help organizations check for ambiguities in running applications or operating systems and other hardware. Using the scanner for these purposes allows the user to work on targeted areas by detecting these flaws quickly and accurately, which would otherwise be a waste of time. It also helps an organization to be scalable and compliant with common information security standards.
TOP 10 of the Right Vulnerability Scanning Tool
Since not all companies and organizations are created equal, so are vulnerability scanners; You can’t find one that fits all. However, when researching the options available, you can look for metrics like accuracy, scalability, reporting, and reliability as per your requirements. Many options are available with unique features. Here is a list of the top ten tools to help you decide which one meets your criteria:
1 Acunetix WVS
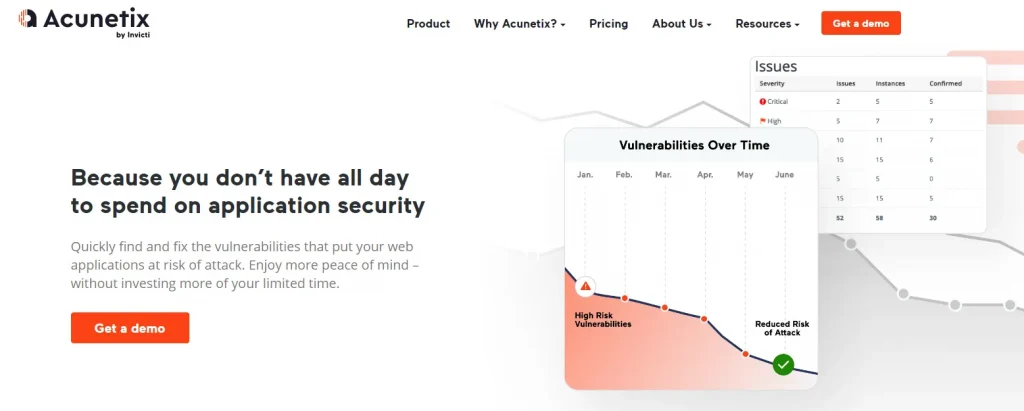
Acunetix WVS is a web vulnerability scanner that automatically inspects web applications. This tool is particularly good at scanning for cross-site scripting vulnerabilities, SQL injection, weak password cracking, and more. Acunetix is used to test whether your website or web application is secure, and find possible SQL injection by scraping and analysis. Through testing, it can list detailed reports and harden web applications accordingly.
Acunetix is not just a web vulnerability scanner. It is a complete web application security testing solution that can be used both stand-alone and as part of complex environments. It offers built-in vulnerability assessment and vulnerability management, as well as many options for integration with market-leading software development tools. By making Acunetix one of your security measures, you can significantly increase your cybersecurity stance and eliminate many security risks at a low resource cost.
Its “Advanced Macro Recording” feature allows Acunetix to scan complex multi-level forms and password-protected pages of a site. It ensures verification of the detected vulnerability to avoid reporting false positives.
Moreover, Acunetix classifies detected vulnerabilities based on their threat level. As such, security teams can prioritize their repose to vulnerabilities that pose a significantly greater threat.
Acunetix also allows you to schedule your scans to initiate automatic scanning at a specified date and time. Alternatively, you can allow Acunetix to continuously scan your system to alert you about detected vulnerabilities in real time.
The platform can generate intuitive regulatory and technical reports that reveal how to remediate the vulnerability.
Features
- Advanced Macro Recording
- Schedule and Prioritize Scan
- Integrate seamlessly with other tracking systems.
- Generate comprehensive reports on detected vulnerability.
Verdict: Acunetix comes with a current version that is capable of performing continuous, automated scans that detect over 7000 different vulnerabilities. Its utilization of interactive application security testing makes it one of the fastest and most accurate vulnerability scanners we have today.
2 AppScan
AppScan provides security testing throughout application development. The tool can also help with security assurance early in the development phase and simplify unit testing. The tool can scan for many common vulnerabilities such as HTTP response splitting, cross-site scripting, hidden field manipulation, parameter tampering, buffer overflows, backdoors/debugging options, and more.
The platform is also capable of large-scale, multi-app, multi-user dynamic application security testing to accurately detect, understand and patch vulnerabilities accurately. HCL AppScan also facilitates cloud-based security testing on web, mobile, and desktop applications due to its utilization of static, dynamic, interactive, and open-source analysis.
Features
- Powerful Cloud-Based Security Testing
- Streamline collaboration between security teams.
- Quick Vulnerability Detection and Fix.
- Presents intuitive reports and analysis on detected vulnerability.
Verdict: HCL ApScan’s agile and powerful security testing system can be built into every phase of your software’s development lifecycle. Its combined static, dynamic, and interactive approach to scanning allow HCP AppScan to detect vulnerabilities accurately and suggest remediation actions without wasting any time.
3 Burp Suite
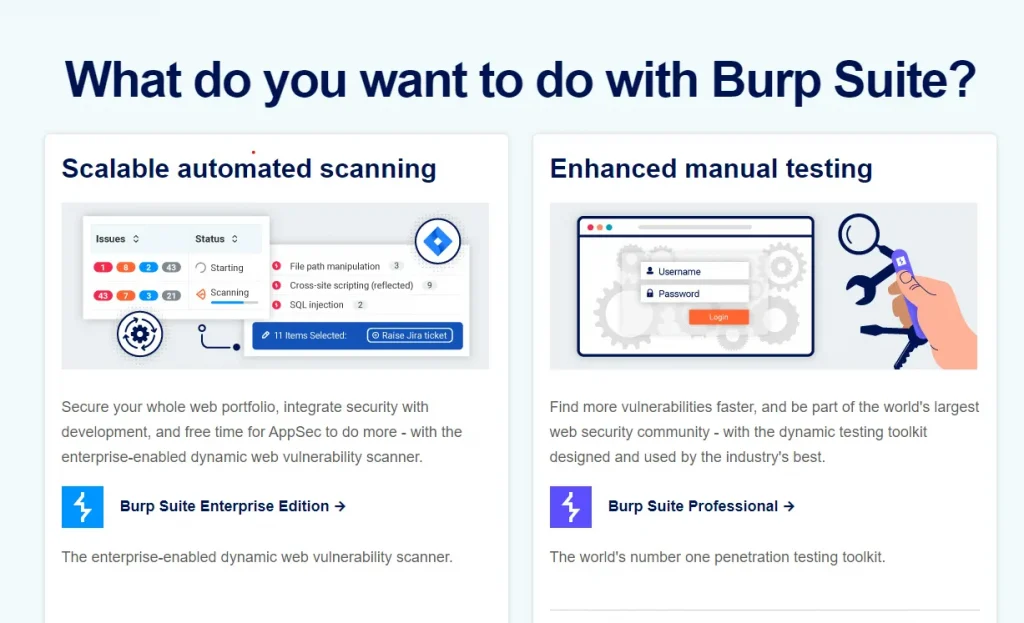
Burp Suite is a platform that contains different types of tools with many interfaces between them designed to facilitate and speed up the process of attacking applications. All these tools share the same framework for displaying and handling HTTP messages, authentication, persistence, logging, alerting, proxies, and extensibility.
Burp Suite is an integrated platform/graphical tool for performing security testing of web applications. Its various tools work seamlessly together to support the entire testing process, from initial mapping and analysis of an application’s attack surface to finding and exploiting security vulnerabilities.
The platform assigns threat levels to all the vulnerabilities it detects so you can prioritize threats that exhibit an urgent threat to your system. It also allows you to schedule your scans at a specified date and time to begin full-scale vulnerability scans automatically. Burp Suite’s current version integrates well with multiple CI/CD tracking systems.
Features
- Automated and Continuous Scanning
- Assign threat levels to detect vulnerability.
- Schedule scans at a specified date and time.
- Integrate seamlessly with third-party tracking systems.
Verdict: Burp Suite’s integration with other powerful tracking systems and its ability to generate detailed reports allows it to accurately detect and remediate vulnerabilities more quickly than most. The platform will satisfy those who wish to constantly monitor their web applications for vulnerabilities.
4 Onsecurity.io
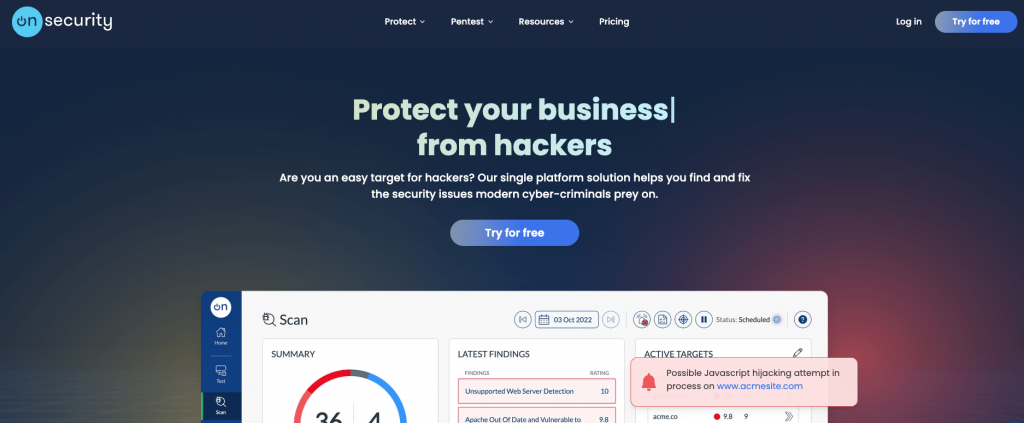
Scan by OnSecurity is a vulnerability scanning tool that finds and reports vulnerabilities in your internet-facing infrastructure before the hackers do, so you can take action and prevent breaches in real-time. How does it work? Scan carries out over 40,000 checks for missing patches, security misconfigurations, default passwords, dangerous services, or potentially harmful security vulnerabilities in your configured targets. OnSecurity monitors your external assets including web applications and web servers. If you’re not sure what your assets include, OnSecurity can identify them for you using Open-Source Intelligence.
The OnSecurity Portal will notify you as soon as a finding is discovered, in-portal, via SMS, or Slack. This will ensure any missing patches linked to vulnerability will be addressed immediately to reduce your risk window. OnSecurity offers a 14-day free trial so you can see if it’s the right fit for your business.
Features:
- Scan runs daily which drastically reduces the window of opportunity.
- Effortless compliance with SOC II Type II, PCI-DSS, and ISO27001 standards.
- Integrate your workflows with Slack, Teams, JIRA and more.
- Easy setup so you can start scanning within seconds.
Verdict: Scan by OnSecurity finds the most dangerous vulnerabilities before the bad guys do. The cutting-edge vulnerability scanning technology works 24/7 so you can get a good night’s sleep. OnSecurity’s actionable findings tell you what the problem is, where it is and what you need to do to take action immediately to fix the problem and stay safe.
5 Nikto
Nikto is an Open Source (GPL) web server scanner which performs comprehensive tests against web servers for multiple items, including over 6700 potentially dangerous files/programs, checks for outdated versions of over 1250 servers, and version-specific problems on over 270 servers. It also checks for server configuration items such as the presence of multiple index files, and HTTP server options, and will attempt to identify installed web servers and software. Scan items and plugins are frequently updated and can be automatically updated.
Nikto is not designed as a stealthy tool. It will test a web server in the quickest time possible and is obvious in log files or to an IPS/IDS. However, there is support for LibWhisker’s anti-IDS methods in case you want to give it a try (or test your IDS system).
Not every check is a security problem, though most are. There are some items that are “info only” type checks that look for things that may not have a security flaw, but the webmaster or security engineer may not know are present on the server. These items are usually marked appropriately in the information printed. There are also some checks for unknown items which have been seen scanned for in log files.
Features
- SSL and Full HTTP Proxy Support.
- Generate reports on detected vulnerability.
- Verify vulnerability to detect false positives.
- Open Source and Free
Verdict: Nikto2 is a free-to-use, open-source vulnerability scanner that can detect a plethora of vulnerabilities in a quick and accurate manner. It requires minimal to no manual intervention as Nikto2 intuitively verifies a vulnerability to report confirmed vulnerabilities, thereby saving time with reduced false positives.
.
6 Netsparker: Called now Invicti
Netsparker is a comprehensive web application security vulnerability scanning tool. It is divided into a professional version and a free version. The free version is also more powerful. A feature of Netsparker compared with other comprehensive web application security scanning tools is that it can better detect security vulnerabilities of SQL Injection and Cross-site Scripting types.
Netsparker’s combined dynamic and interactive (DAST+IAST) approach to scanning allows it to detect vulnerabilities faster and more accurately.
Moreover, the platform verifies all detected vulnerabilities in an open, read-only manner, thereby eliminating false positives. The tool makes managing vulnerabilities simpler because of its visual dashboard.
The dashboard can be used to manage user permissions or assign vulnerabilities to specific security teams. Furthermore, Netsparker is capable of automatically creating and assigning confirmed vulnerabilities to developers as well. The platform also provides you with detailed documentation on detected vulnerabilities.
The reports generated to allow you to pinpoint the location of the vulnerability and remediate it as quickly as possible. Netsparker also integrates seamlessly with other third-party tools like Okta, Jira, GitLab, and more.
Features
- Combined DAST+ IAST Scanning.
- Advanced Web Crawling
- Proof Based Scanning to detect false positives.
- Detailed documentation on detected vulnerability.
- Manage user permissions and assign vulnerability to security teams.
7 BeEF

BeEF is a complete Browser Exploitation Framework, which is an excellent professional security tool. This tool will provide groundbreaking technical support for experienced penetration testers. Unlike other tools, BeEF focuses on exploiting browser vulnerabilities to check the security posture of a target. This tool was created for penetration testing and legitimate research.
Amid growing concerns about web-borne attacks against clients, including mobile clients, BeEF allows the professional penetration tester to assess the actual security posture of a target environment by using client-side attack vectors. Unlike other security frameworks, BeEF looks past the hardened network perimeter and client system, and examines exploitability within the context of the one open door: the web browser. BeEF will hook one or more web browsers and use them as beachheads for launching directed command modules and further attacks against the system from within the browser context.
8 Dradis
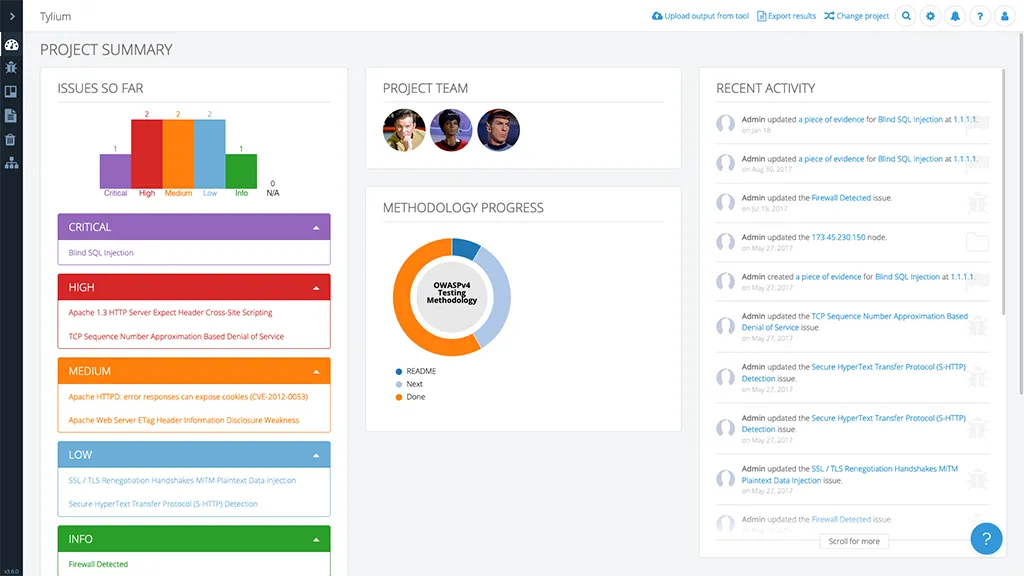
Dradis is an open source tool that enables users to efficiently share information and data, especially during security assessments. Features include simple report generation, attachment support, integration with existing systems and tools via server plugins, and platform independence.
9 Metasploit

Metasploit is an open source security exploit and testing tool that integrates common overflow vulnerabilities and popular shellcodes on various platforms and is continuously updated. Metasploit covers the entire process of penetration testing. You can use existing payloads to perform a series of penetration tests under this framework.
10 sqlmap
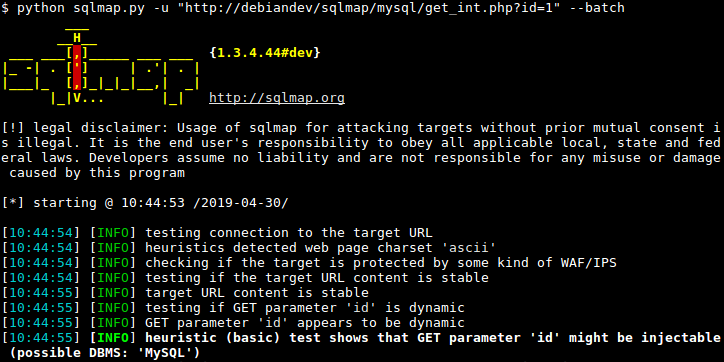
sqlmap is an open source tool that can automatically detect and exploit SQL injection vulnerabilities and take over database servers. It includes a powerful detection engine, many niche features for the ultimate penetration tester, and various toggles from database fingerprinting and fetching data from the database to accessing the underlying filesystem and executing commands on the operating system via output.
11 10. w3af

w3af is one of the most popular, flexible, and powerful tools for finding and exploiting web application vulnerabilities. It is very easy to use and offers dozens of development features and web evaluation plugins. Others call it web-centric Metasploit. w3af is divided into two main parts, core, and plugin. Plugins are divided into different types, they are discovery, brute force, audit, evasion, grep, attack, export, and sabotage.



























